A mobile device can be compromised if unauthorized agents gain super-user access permissions to the system files that control device operation and data access. This loss of control is possible if a device user roots their device to get full control over the device firmware, files, UI, and apps. Malware can exploit this vulnerability to steal passwords, hijack identities, access secret info, install apps, and modify firmware.
Enterprises with Bring Your Own Device programs are especially at risk, as employees may potentially use rooted Android devices in the workplace. Risks range from the exposure of confidential enterprise assets to wider attacks on enterprise resources and infrastructure. Enterprises must have a fail-safe way to detect if a device is compromised before allowing device users to deploy it in the workplace.
Reliable detection of compromised devices
Malware can potentially intercept and forge the results of a device health check, making a compromised device seem secure. The Knox platform leverages its hardware-backed trusted environment to reliably detect and report compromised devices.
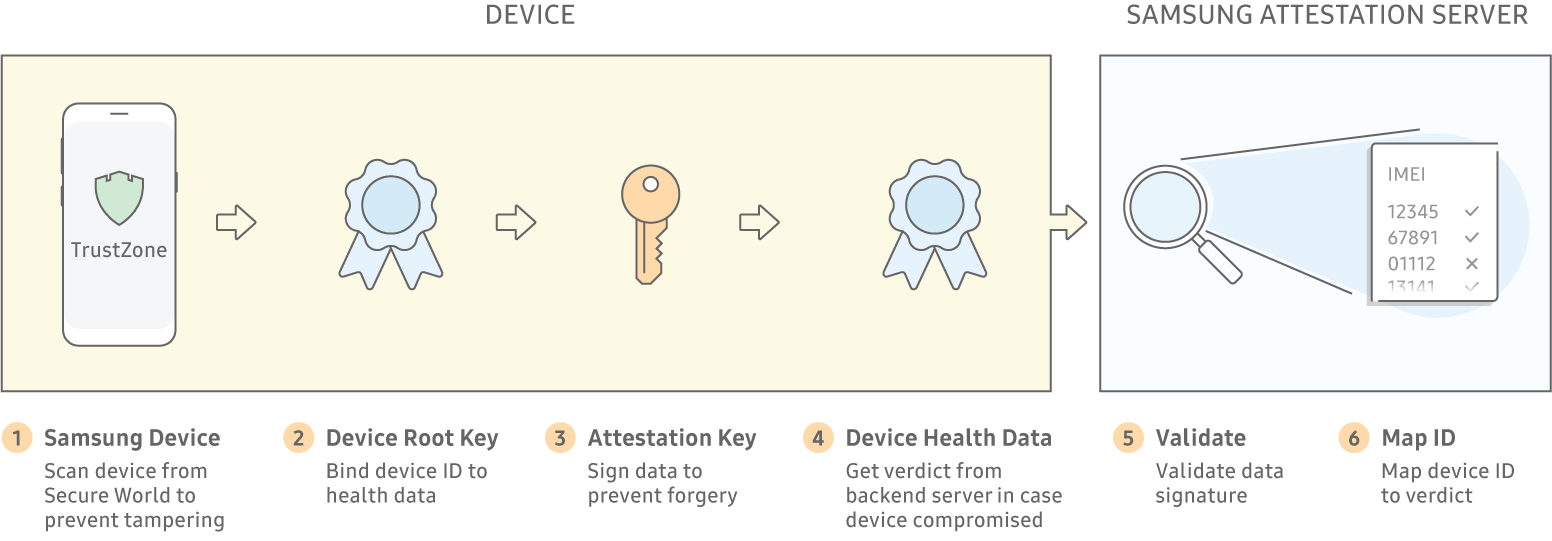
Because a Device Root Key (DRK) is unique to each device, it can tie data to a device through cryptographic signatures. The Samsung Attestation Key (SAK) signs the Attestation data to prove that it originated from the TrustZone Secure World on a Samsung Knox device.
Knox Attestation works in tandem with Trusted Boot and Periodic Kernel Measurements to ensure the integrity of devices during deployment, bootup, and operation.
How Knox Attestation works
- A device check is initiated by either:
- An enterprise IT admin using an EMM console
- A web script executing a regularly scheduled check
- The web server that initiated the check requests a nonce from Samsung's Attestation server. A nonce is just an arbitrary number used in cryptographic communication to uniquely identify each attestation result.
- The web server instructs the device to begin a check, passing the nonce as a check identifier.
- A Knox Attestation agent on the device operates within the Secure World partition within the ARM TrustZone to create a blob, that is, a binary large object. This blob is a snapshot of the device's current state. It contains data about whether the device was ever rooted, or if the device has a bootloader or firmware file that was not factory installed or part of an official upgrade.
- Samsung's Attestation server validates the data signature on the blob to ensure that it was from a trusted Samsung source, analyzes the blob data, and derives a verdict indicating whether or not the device is compromised.
- The original requestor of the device check can quickly take action, for example,
- Report the verdict to the device user.
- Immediately prevent the device from accessing enterprise systems.
- Uninstall any enterprise apps or assets already on the device.
Highly secure or firewalled operations that do not want to access Samsung's web-based Attestation server can install an Attestation Validator tool onto a local server to parse blobs and keep device verdicts within the firewall.
Unique advantages of Knox Attestation
Knox Attestation provides these key differentiators:
- Health measurements guaranteed per device, through a Device Root Key.
- Health results that easily map to device identifiers like an IMEI.
Unlike other solutions on the market, Knox Attestation enables IT admins to determine which attestation result correlates with which device, without having to painstakingly map IDs manually. With competitor solutions, results are returned for separate devices, but IT admins can't differentiate between devices, and consequently the results are not actionable. Knox Attestation returns a single device ID and enables IT admins to prevent or contain issues promptly.
Next steps
- Read the Samsung Knox White Paper
- Learn more about Knox Platform for Enterprise
- Join the Samsung Enterprise Alliance Program